-
Aes Key Generation In Python카테고리 없음 2021. 1. 13. 22:03
The main thing that changes in AES is how you generate the key schedule from the key — an issue I address at the end of Section 8.8.1. The notion of key schedule in AES is explained in Sections 8.2 and 8.8. Encryption consists of 10 rounds of processing for 128-bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys. AES key expansion consists of several primitive operations: Rotate – takes a 4-byte word and rotates everything one byte to the left, e.g. Rotate(1,2,3,4) → 2, 3, 4, 1 SubBytes – each byte of a word is substituted with the value in the S-Box whose index is the value of the original byte. AES-128 has 128 bit key = 16 bytes. Randomkey = os.urandom(16) should be sufficient for most uses. When you feed this random value to M2 (or whatever crypto library), it is transformed internally into a 'key schedule' actually used for encryption. Activate windows 8.1 key generator reddit download.
- Cryptography Tutorial
- Cryptography Useful Resources
- Selected Reading
The more popular and widely adopted symmetric encryption algorithm likely to be encountered nowadays is the Advanced Encryption Standard (AES). It is found at least six time faster than triple DES.
This article discusses how to generate an unencrypted private key and public certificate pair that is suitable for use with HTTPS, FTPS, and the administrative port for EFT Server. (To generate an encrypted key/certificate pair, refer to Generating an Encrypted Private Key and Self-Signed Public Certificate.) General Information. Generate unencrypted private key openssl. To generate public (e,n) key from the private key using openssl you can use the following command: openssl rsa -in private.pem -out public.pem -pubout To dissect the contents of the private.pem private RSA key generated by the openssl command above run the following (output truncated to labels here). Generate OpenSSL RSA Key Pair from the Command Line. You can generate a public and private RSA key pair like this. Inspecting the output file, in this case privateunencrypted.pem clearly shows that the key is a RSA private key as it starts with -BEGIN RSA PRIVATE KEY-.
A replacement for DES was needed as its key size was too small. With increasing computing power, it was considered vulnerable against exhaustive key search attack. Triple DES was designed to overcome this drawback but it was found slow.
The features of AES are as follows −
- Symmetric key symmetric block cipher
- 128-bit data, 128/192/256-bit keys
- Stronger and faster than Triple-DES
- Provide full specification and design details
- Software implementable in C and Java
Operation of AES
AES is an iterative rather than Feistel cipher. It is based on ‘substitution–permutation network’. It comprises of a series of linked operations, some of which involve replacing inputs by specific outputs (substitutions) and others involve shuffling bits around (permutations).
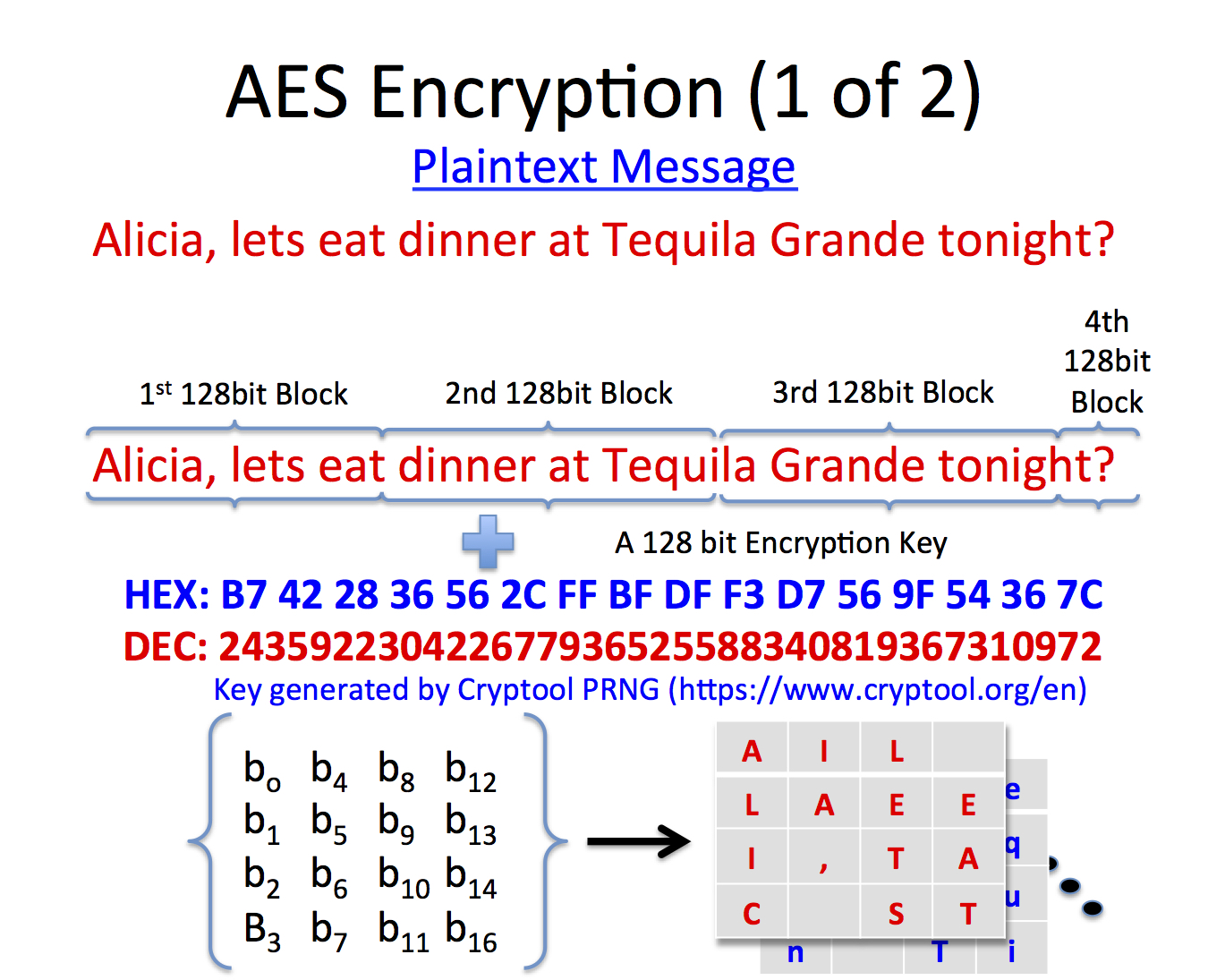
Interestingly, AES performs all its computations on bytes rather than bits. Hence, AES treats the 128 bits of a plaintext block as 16 bytes. These 16 bytes are arranged in four columns and four rows for processing as a matrix −
Unlike DES, the number of rounds in AES is variable and depends on the length of the key. AES uses 10 rounds for 128-bit keys, 12 rounds for 192-bit keys and 14 rounds for 256-bit keys. Each of these rounds uses a different 128-bit round key, which is calculated from the original AES key.
The schematic of AES structure is given in the following illustration −
Encryption Process
Here, we restrict to description of a typical round of AES encryption. Each round comprise of four sub-processes. The first round process is depicted below −
Byte Substitution (SubBytes)
The 16 input bytes are substituted by looking up a fixed table (S-box) given in design. The result is in a matrix of four rows and four columns.
Shiftrows
Each of the four rows of the matrix is shifted to the left. Any entries that ‘fall off’ are re-inserted on the right side of row. Shift is carried out as follows −
First row is not shifted.
However the game is no longer listed on the Strategy First site so it is no longer possible to get support from them using the site. Steam keep going round in circles with this and Im no further on than I was when I reported the issue a month ago today.I have contacted Strategy First and they acknowledged responsibility for support for the game dispite it not being listed on their site and are presently working on the problem. I just recently sent them my DX diagnostic test report and an update on a missing.exe file I noticed in the game folder that I remember was there before this most recent STEAM update was forced on those of us who have the game. Deep black reloaded serial key generator.
Second row is shifted one (byte) position to the left.
Third row is shifted two positions to the left.
Fourth row is shifted three positions to the left.
The result is a new matrix consisting of the same 16 bytes but shifted with respect to each other.
MixColumns
Each column of four bytes is now transformed using a special mathematical function. This function takes as input the four bytes of one column and outputs four completely new bytes, which replace the original column. The result is another new matrix consisting of 16 new bytes. It should be noted that this step is not performed in the last round.
Addroundkey
Pure Python Aes
The 16 bytes of the matrix are now considered as 128 bits and are XORed to the 128 bits of the round key. If this is the last round then the output is the ciphertext. Otherwise, the resulting 128 bits are interpreted as 16 bytes and we begin another similar round.
S-des key generation code in java download. You'll need to pad out the string (using the PKCS#7 standard, preferably) to a multiple of the block length: plaintext = pr.exportKey('PEM')remainder = len(plaintext)% descipher.blocklengthif remainder:# add paddingpadlength = des.blocklength - remainderplaintext += chr(padlength). externKey (string) - The RSA key to import, encoded as a string.Next, you can't encrypt the RSA private key object. You can only encrypt bytes, so export the private key again. Read the file: pr = RSA.importKey(open('mykey.pem', 'r').read)or, using a context manager to close the file properly: with open('mykey.pem', 'r') as keyfile:pr = RSA.importKey(keyfile.read)Using the files as context managers removes the need to call close on each of them at the end.From the:importKey(externKey, passphrase=None)Import an RSA key (public or private half), encoded in standard form.Parameters:.
Free Key Generation Software
Decryption Process
The process of decryption of an AES ciphertext is similar to the encryption process in the reverse order. Each round consists of the four processes conducted in the reverse order −
- Add round key
- Mix columns
- Shift rows
- Byte substitution
Since sub-processes in each round are in reverse manner, unlike for a Feistel Cipher, the encryption and decryption algorithms needs to be separately implemented, although they are very closely related.
AES Analysis
Aes Key Generation In Python Free
In present day cryptography, AES is widely adopted and supported in both hardware and software. Till date, no practical cryptanalytic attacks against AES has been discovered. Additionally, AES has built-in flexibility of key length, which allows a degree of ‘future-proofing’ against progress in the ability to perform exhaustive key searches.
Python Aes Doc
However, just as for DES, the AES security is assured only if it is correctly implemented and good key management is employed.